Managing Firewall Rules
ShellHub provides flexible firewall for filtering SSH connections. It gives a fine-grained control over which SSH connections reach the devices.
Using Firewall Rules you can deny or allow SSH connections from specific IP address to a specific or a group of devices using a given username.
info
This feature is only available in ShellHub Cloud and ShellHub Enterprise.
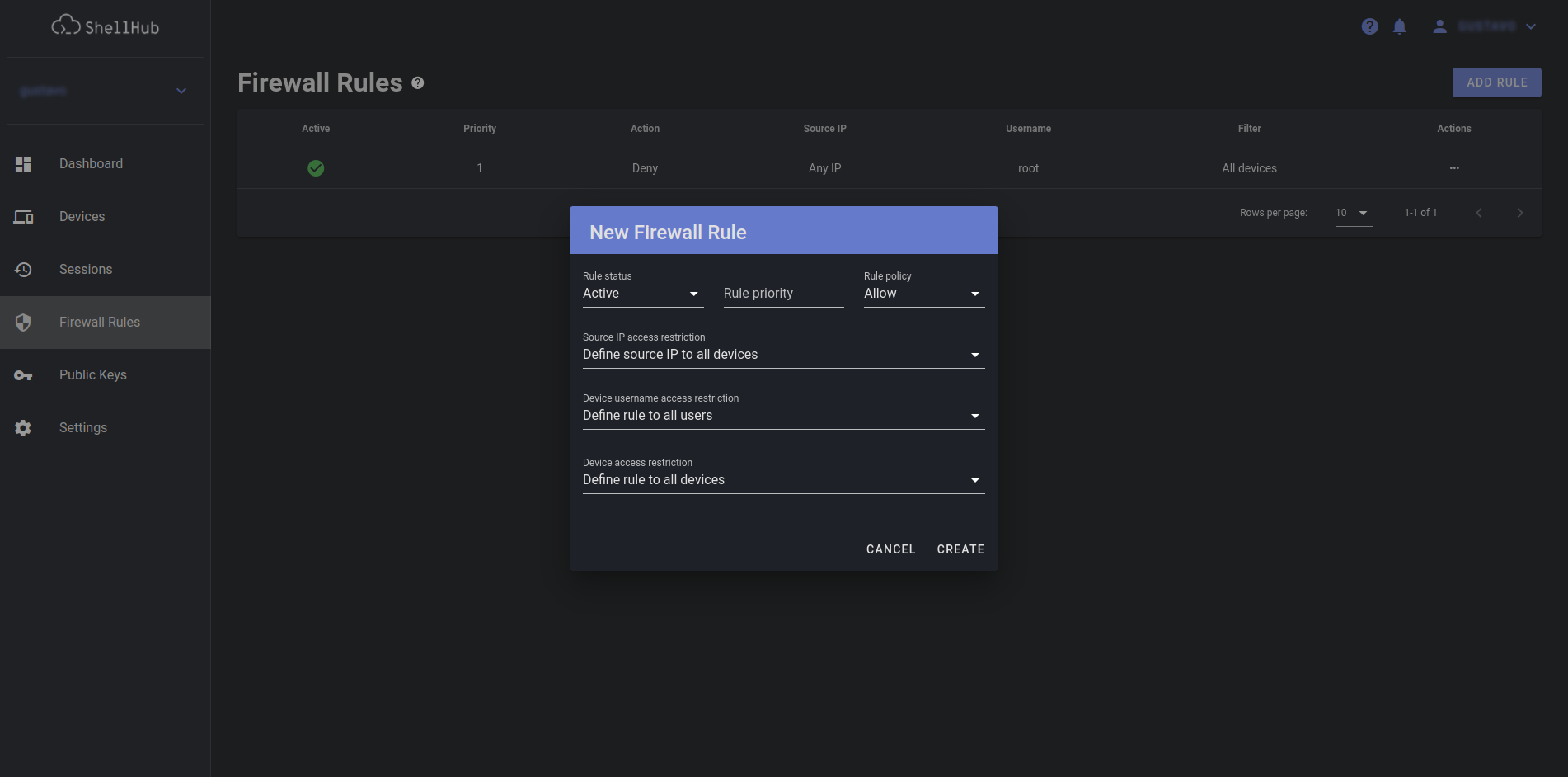
Create a firewall rule
From the Firewall Rules page, click Add Rule and fill the form.